Stepping into the realm of AWS Key Management Service (KMS) is like finding the key to a treasure chest of robust security for your data.
Businesses today can't overlook data encryption, and AWS KMS shines brightly in this field.
Importance of Data Encryption
Why is data encryption so vital? Using AWS KMS for encryption brings along a host of benefits that are simply irresistible. In our digital era, shielding sensitive data is crucial, and AWS KMS offers solid security.
It's about making sure that your data's access keys remain in safe and reliable hands.
What is AWS KMS?
AWS Key Management Service (KMS) is an impressive tool from Amazon Web Services.
It simplifies creating and handling encryption keys, keeping your data protected. Picture having the strength to make, manage, and oversee the keys that secure your information.
These keys are safeguarded by top-of-the-line FIPS 140-2 validated hardware security modules.
AWS KMS isn't just about key encryption; it's about mastering the art of managing encrypted keys efficiently.
Why Choose AWS KMS?
Why opt for AWS KMS over other encryption tools? The advantages of AWS KMS are evident.
It's not merely about when to use it; it's about having control with customer-managed keys and convenience with AWS-owned keys.
Often, the keys you design with AWS KMS are customer-managed, which affords you extraordinary control.
If ease is your priority, AWS services using KMS can automatically generate these keys for you.
This blend of flexibility and security makes AWS KMS a top choice for data encryption.
For those who appreciate control mixed with simplicity, AWS KMS is an ideal match. It enables you to effortlessly manage and protect your encryption keys—a perfect tool for anyone committed to safeguarding their digital treasures.
Implementing Data Encryption with AWS KMS
Welcome! Today, we're diving into the world of data encryption with AWS KMS.
If you’ve ever felt overwhelmed by managing encryption keys, you're in the right place.
By the end of this guide, you’ll feel confident and well-equipped to handle data encryption with AWS KMS.
How AWS KMS Works
At its core, AWS KMS makes encryption and key management a breeze. It's like having a security expert right by your side, managing your encryption needs.
Key Types and Uses
AWS KMS is versatile. It provides two types of encryption keys: symmetric and asymmetric.
You can create these keys using the AWS Management Console or an API.
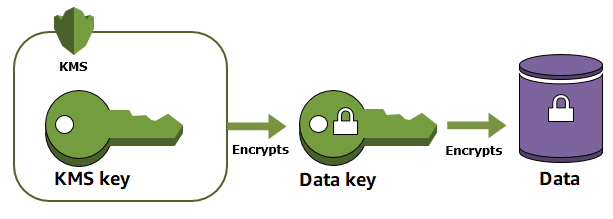
The stars of the show are Customer Master Keys (CMKs) and Data Keys. CMKs handle encryption and decryption of data up to 4 kilobytes, and they're also vital for dealing with Data Keys.
Stepping into AWS KMS feels like entering a realm where encryption becomes simple and secure.
Here's a handy guide to the key hierarchy:
AWS KMS Encryption Process
Think of the AWS KMS encryption process as a graceful dance of security measures. When KMS encrypts an object, it creates ciphertext that includes a reference to the Hardware Security Module (HSM) backing key.
This is crucial for decryption later on.
In practice, AWS KMS generates a unique data key for your data.
This key is encrypted using a CMK, which then safeguards your data. Just like that, your data is secured with impressive encryption.
Setting Up AWS KMS
Setting up AWS KMS is smooth and straightforward.
There are a few network requirements to consider, like TCP/IP connectivity and DNS configurations. You can set it up via the AWS Management Console or by using an API.
The real charm of AWS KMS is its seamless integration with other AWS services. It's a must-have tool in your security arsenal.
Ready to dive in? A detailed AWS KMS integration guide is waiting to assist you.
With AWS KMS, complexities fade away, offering you secure and user-friendly encryption management.
Strategies and Best Practices
Diving into AWS KMS encryption can feel like walking through a puzzle. But, knowing the top strategies and best practices can really up your security game.
Encryption Solutions
Ever curious about the difference between a data key and a KMS key? Think of KMS keys as the real guardians.
They generate, store, and manage encryption keys securely. These keys never leave the KMS unencrypted.
On the other hand, data keys are your go-to tools for encrypting and decrypting data. They work with both symmetric and asymmetric encryption schemes.
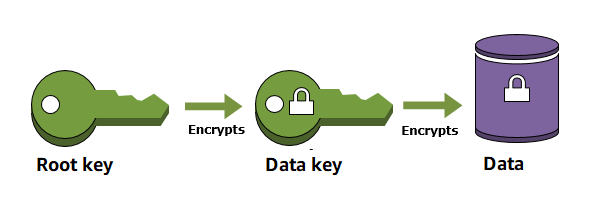
So, does KMS use envelope encryption? You bet it does! Here's how: First, a Data Encryption Key (DEK) is generated locally.
It's used to encrypt your data. Then, it's wrapped with a Key Encryption Key (KEK). Both the secured DEK and the encrypted data are stored together. This layering keeps your data super safe.
KMS Security Features
AWS KMS boasts top-notch security features that really shine.
A standout strategy is all about protecting imported key material as it travels to AWS KMS. It uses a public key from an RSA key pair, created in an AWS KMS HSM, to encrypt key material.
Once it’s decrypted, it gets re-encrypted under a symmetric key in the HSM. Pretty powerful, right?
Wonder how S3 KMS encryption works? When S3 needs a data key, it knocks on KMS’s door.
KMS then provides both the plaintext data key and its encrypted version.
S3 uses the plaintext data key to encrypt the object and saves the encrypted object and data key to disk.
Neat, huh? This ensures everything in S3 stays locked up tight.
Comparing AWS KMS with Other Services
What makes AWS KMS stand out compared to other encryption services? One big difference is how KMS and Secrets Manager handle encryption.
Secrets Manager uses plaintext data keys and the AES algorithm to encrypt secret values outside.
Meanwhile, KMS manages these tasks within its realm, creating an extra layer of security.
Thinking about the differences between KMS and Secret Manager? Here's a quick tidbit: Both services use encryption to protect sensitive bits, but KMS mainly focuses on managing keys.
It ensures they stay protected within the KMS environment.
Secrets Manager, however, encrypts secret values outside of KMS using unique methods, retaining encrypted copies for security.
AWS KMS is your all-in-one solution for data security.
It efficiently manages both encryption solutions and robust security features. This makes it invaluable for anyone serious about data protection.
Now, with these insights, you're all set to optimize your AWS KMS efforts!
Conclusion
Let's wrap up with a quick look at the key insights we've gathered from diving into AWS KMS encryption.
Implementing AWS KMS for Enhanced Security
Choosing to use AWS KMS encryption isn't just a tech choice—it's a smart move to boost security across your digital landscape.
AWS Key Management Service isn't just about keeping your data safe; it centralizes key management, which is a huge help.
Plus, it automatically rotates your keys, adding a protective layer to your sensitive data.
In my own experience, using AWS KMS has really simplified how we handle key management. It also makes compliance much less of a headache.
We've learned to pick the right KMS practices, keeping our data safe and private. When done right, this service can truly transform how organizations protect their digital assets.
When I first started exploring AWS Key Management Service (KMS), I was amazed by its sophisticated and powerful features.
With the rising need for secure cloud solutions, using AWS KMS correctly can be a real game-changer for you!
Exploring Advanced Security Features of AWS KMS
AWS KMS isn't just a typical encryption service; it’s the heavyweight champion of security. What makes it shine are its advanced security layers.
These include envelope encryption, seamless integration with other AWS services, and strong access controls.
Did you know that AWS KMS can handle billions of encryption requests per second? It’s not just impressive—it's crucial for businesses dealing with large volumes of sensitive data.
Pro Tip: Try implementing envelope encryption as a layered security approach and watch the magic happen!
Comparing AWS KMS with Other Cloud Encryption Solutions
Wondering how AWS KMS stands against its competitors? It’s worth considering. While services like Google Cloud KMS and Azure Key Vault have similar features, AWS KMS outshines them.
Why? It’s easy to use, cost-effective, and part of a vast ecosystem of integrated services.
From what I’ve heard—and yes, it's from the cybersecurity grapevine—AWS KMS often leads in reliability and scalability.
Plus, let's not forget AWS's strong customer support and continual innovation!
Step-by-Step Guide to Configuring AWS KMS for Cloud Storage
Here's the big question: How do you configure AWS KMS for cloud storage like a pro?
Start by creating a customer master key (CMK) in your AWS Management Console.
Once that’s done, grant the necessary privileges to access and manage your keys effectively.
AWS makes the process seamless. It maps easily to your existing security infrastructure.
If you follow each step carefully, you’ll unlock the full potential of AWS KMS, revolutionizing your data storage and management with top-notch security.
By understanding and using AWS KMS’s features, you can not only improve your data management practices but also strengthen your entire cloud environment with improved security measures.
Ready to explore further? Check out related guides and tutorials, like our detailed comparison of AWS KMS with other solutions, for a broader view of cloud encryption possibilities.